Imagine this. You are drinking your Sunday morning coffee when you see in the news that hackers took control of a connected device. As the reporter tells the story and recounts the damages, you realize they are talking about your product! Hackers exploited a security hole you didn’t know you have. Things are not looking good for you or your product!
The reason I put you in the center of this scenario is to help you realize that thinking, “It’ll never happen to me,” can get you in trouble.
Think about it: before IoT, a cyber attack would focus on denial of service, millions of dollars lost in sales, identity theft, stolen credit card or social security numbers, etc.
But since IoT provides access to real-world objects, then an attack can cause real-world harm to people, and even result in loss of life.
Consider these scenarios. What if hackers take control of:
- An elevator at a skyscraper, trapping all passengers
- Self-driving cars – here’s a very scary experiment of hacking a car in motion
- The controller of an aircraft turbine, forcing it to malfunction
- A robotic arm at a factory, instructing it to hit everything around it
- The locks of all the doors in a smart home, making it vulnerable to intruders
- Medical equipment at a hospital, harming the people connected to them
This is why security must be top of mind. Attacks are very real, and we need to stay one step ahead. Instead of being an afterthought, security should be embedded in the way you build IoT products.
But as a Product Manager, you are probably not a security expert. So where do you start tackling such a big topic?
Evaluate Security at Each Layer of the IoT Stack
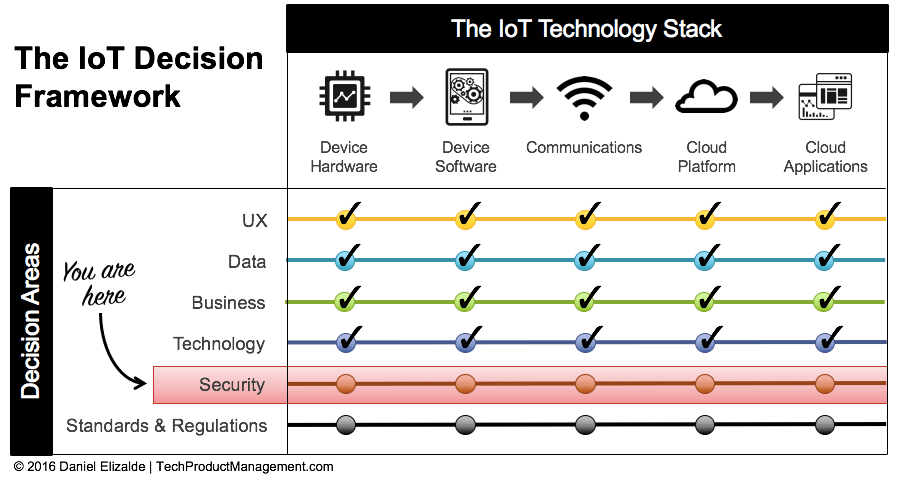
The term “security” is a big nebulous thing, so it’s hard to know where to start. That’s why I’ve included security as a Decision Area in my IoT Decision Framework. By evaluating security at each layer of the IoT stack, you’ll have a more focused view and will be able to plan an actionable security roadmap.
Related post: Take Control of Your IoT Strategy with the IoT Decision Framework.
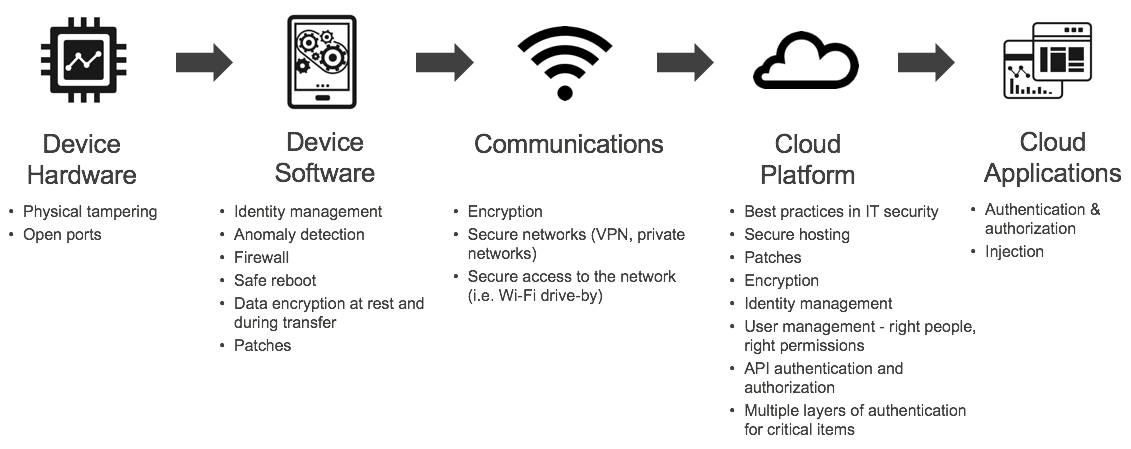
Based on the IoT Technology Stack, the two key security vectors you need to protect are:
- Physical tampering at the devices layer
- Cybersecurity across the other four layers (embedded software, communications, cloud platform, and applications)
1. Protect Against Physical Tampering
With IoT, we are installing millions of devices within hand’s reach, which opens a new opportunity for hackers to tamper with the device and get control of it.
Here’s a real-world example: A hospital invested millions of dollars in cybersecurity to prevent unauthorized access to their network. To their surprise, not long after the security revamp was completed, they found a Trojan horse in their network. The head of cybersecurity was appalled and couldn’t figure out where the attack came from since all the possible cyber attack points were protected. Servers were patched, passwords were enforced, firewalls were in place, you name it.
So how did the attackers get into the hospital’s network?

Here’s the kicker. One day, an unsuspecting nurse decided to charge her Android phone using one of those USB ports. The phone had a Trojan horse that found its way into the hospital network. Oops.
Every time I go out, I’m amazed by the number of easily accessible ports (USB, SD Cards, Ethernet, etc.) that you find all over the place, in hospitals, airports, retail businesses, and more. It’s scary when you start paying attention.
Physical tampering can be done a lot of different ways. It includes anything from connecting to exposed ports, to interrupting the device’s power, device theft, removing parts, etc.
As a Product Manager, you’ll need to come up with your own analysis of how someone could tamper with your device. Start by thinking:
- What would happen if somebody gets physical access to my device?
- What type of damage could they do?
- Would they be able to use that as a backdoor into my system or my customer’s network?
Then think about how you can prevent those attacks. Here are some concrete examples:
- Ensure your product has no exposed ports or connectors.
- Implement locks or other ways to ensure that only authorized people can get access to your product.
- As much as possible, plan for your product to be installed outside normal reach (for example, in a secure room or on a tall ceiling).
2. Protect Against Cybersecurity Attacks
Standard cybersecurity practices apply to all the remaining layers of the IoT stack: from embedded software all the way to applications. As Product Manager, your role is to make sure security is consistent across the full stack since different layers of the stack are often developed by different engineering teams.
Cybersecurity has many considerations, ranging from encryption to identity management, authentication, authorization, etc. My advice is to walk the IoT Technology Stack with your team and evaluate what the risks and vulnerabilities are at each layer of the stack.
Then outline the steps you need to take to protect each layer of the stack. The result could look something like this:
The Bottom Line
As an IoT Product Manager, your goal is not to be the security subject matter expert. Instead, your goal is to ensure security is accounted for at each layer of the IoT stack by tackling physical tampering and cybersecurity vulnerabilities.
By using the IoT Decision Framework to identify areas of risk, you’ll be able to identify gaps and create a strategy to secure your product.
Also, remember that security is not a one-time thing. Hackers are always looking for new ways to exploit vulnerabilities and cause harm, so security needs to become a standard part of building and managing your product.
In future posts, I’ll give tips on making sure your product doesn’t get hacked from within your own company. Subscribe to be notified as soon as new posts are released. (Your email is never shared, and you can unsubscribe at any time.)
If you enjoyed this post, I’d really appreciate if you share it with your network!
6 Comments
We are currently not secure on any online platform. Hackers play with your information all the time. They can hack anyone’s data at any moment. So we should make all types of accounts more secure. In particular, the security of online businesses should be taken care of
Thank you for sharing this content. It will be really helpful for us to understand IOT securtiy and hacks.
I’m flattered by the details you have provided on this site. Thank you for sharing the informative content.It may helps to know more about IOT securtiy and hacks. Great article!
A great article about IoT safety. You have almost completed al points about safety. Thanks for sharing
A great article about IoT safety. I loved all the points about saving IoT products from hackers! Keep sharing such useful information.
When it comes to preventing security hacks, there are many technological measures that can be taken. For me, the most important ones are multi-factor verification and the utilization of strong passwords. These measures tend to be the strongest when preventing any kind of cyberattack.